Antiquated CHM Help File Used to Spread CryptoWall Ransomware Spam Attacks
 In today's age, you would think that hackers have moved beyond their old ways of spreading computer viruses and malware onto computers around the world. As it turns out, they are taking to old techniques using old file formats to spread new Ransomware threats, such as the famous CryptoWall Ransomware infection.
In today's age, you would think that hackers have moved beyond their old ways of spreading computer viruses and malware onto computers around the world. As it turns out, they are taking to old techniques using old file formats to spread new Ransomware threats, such as the famous CryptoWall Ransomware infection.
Hackers and cybercrooks are indulging in malicious activities using old techniques, one that uses an old CHM help file format in emails, to spread the CryptoWall Ransomware threat. If you are of the proper age and have used computers for a couple decades now, you may remember the old CHM (Compiled HTML Help) file format, which were files introduced in 1997 as a way to simplify navigation and construction of Windows help files. Such files were an essential part of Windows 98, 2000, ME and XP. Moreover, these help files were a key part of Internet Explorer versions 4 through 6.
CHM files were at one time exploited by hackers unleashing many security holes eventually forcing Microsoft to abandon the file format with the release of Windows Vista in 2007. However, as early as a year ago the CHM file was still lingering on as Microsoft published official documentation in CHM format. Even so, Windows 8.1 has no problem displaying and loading Lync Server 2013 documentation, which was a proponent of using CHM type files.
With CHM files still being a resurrected file format just over a year ago, hackers are utilizing such a file to attach in spam messages blasted in attack waves to numerous computer users. The attachment, as a CHM file, is easily accessed without any apparent road blocks. What is taking place lately is the spam emails containing malicious CHM files are being executed where they will automatically load malware on a victim's computer and encrypt its contents.
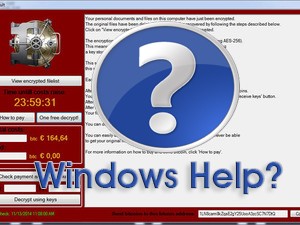
The discovery of malicious CHM files has led computer security researchers down an interesting path, one that has uncovered the infamous CryptoWall Ransomware threat as the executed malware within these malicious CHM files.
There is no doubt that the way hackers have conjured up this scheme to spread CryptoWall through an ancient file format is clever. Because virtually any version of Windows has no issue opening up a CHM file, it is an easy way for hackers to mask the malicious code that injects CryptoWall. As the computer security community knows, CryptoWall is a vicious ransomware threat that makes claims to an infected computer having its files encrypted. The threat may offer ways to decrypt your files through a payment processed via Bitcoins, MoneyPak, Paysafecard, CashU or Ukash. Either way, paying the fine that it asks for, sometimes upwards of $10,000, may or may not grant you a decryption key that it promises. Fundamentally, systems that are infected with CryptoWall are susceptible to their files being permanently damaged and unrecoverable unless you have a separate backup.
So far, the last rash of spam messages launching the malicious CHM file attack to spread CryptoWall was initiated in February of 2015. The spam servers appear to be located in Australia, India, Romania, Spain and the U.S. It is possible that we have not seen the last of this CHM file exploitation nor the ruthless CryptoWall Ransomware threat.