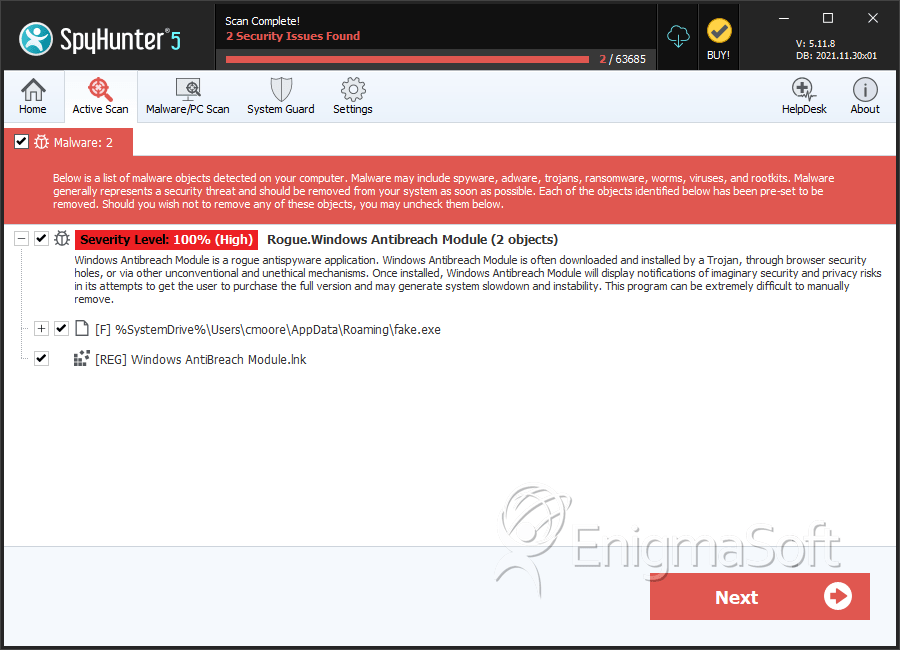
Windows Antibreach Module
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 16,083 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 14 |
| First Seen: | November 21, 2014 |
| Last Seen: | May 6, 2024 |
| OS(es) Affected: | Windows |
Windows Antibreach Module is a fraudulent anti-spyware product known to belong to the FakeVimes family of threats. Within this family of threats, the Windows Antibreach Module program uses the same interface as other applications that ill-minded persons have marketed as programs designed to detect and remove threats on a PC. The catch with Windows Antibreach Module is that Windows Antibreach Module does exactly the opposite; Windows Antibreach Module is the actual infection present on your computer. Windows Antibreach Module do not have the ability to remove real threats from any system. Windows Antibreach Module is basically designed by hackers who want to take money from naive computer users. To accomplish its intent, Windows Antibreach Module does whatever it takes to convince the affected computer user to purchase its good for nothing security program.The best approach to take when Windows Antibreach Module is installed on a computer is to obtain a trusted anti-malware program to remove Windows Antibreach Module at once.
Other applications that belong to the Windows Antibreach Module family include Virus Melt, Presto TuneUp, Fast Antivirus 2009, Extra Antivirus, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, PC Live Guard, Live PC Care, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security, Windows Protection Suite, Windows Work Catalyst.
Table of Contents
SpyHunter Detects & Remove Windows Antibreach Module
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | svc-kyqr.exe | ba4332c134a70ecdd130468f2cfa2c81 | 7 |
| 2. | %AllUsersProfile%\Start Menu\Programs\Windows AntiBreach Module.lnk | ||
| 3. | %UserProfile%\Desktop\Windows AntiBreach Module.lnk | ||
| 4. | %AppData%\data.sec |
