Updated Zeus Trojan and MWI Exploit Kit Used in Targeted Israeli Public Sector Attack
 The Zeus Trojan malware threat, ever since its conception nearly eight years ago, has been one of the top banking malware that cybercrooks utilize for aggressively stealing online account login details. Within Zeus' destructive path many online banking users, as well as many online banking institutions, have succumbed to relinquishing massive amounts of personal data that lead to the theft of money.
The Zeus Trojan malware threat, ever since its conception nearly eight years ago, has been one of the top banking malware that cybercrooks utilize for aggressively stealing online account login details. Within Zeus' destructive path many online banking users, as well as many online banking institutions, have succumbed to relinquishing massive amounts of personal data that lead to the theft of money.
In what appears to be an isolated series of attacks, security experts discovered the Zeus Trojan being used to target the Israeli public sector to steal data. Attackers were able to deliver a modified version of Zeus onto infected and vulnerable computers.
The researchers from the firm Check Point, uncovered the operation after one of its high-profile clients submitted a suspicious RTF file for analysis, which later revealed that the file was sent through spam email to multiple staff members who later opened and executed the attachment. As you would guess, the RTF file attached to the spam messages was infected with a malicious threat.
The threat discovered within the infected RTF files was the Microsoft Word Intruder kit (MWI exploit kit), which is a well-known package that specifically targets Word files on Windows PCs. Use of the exploit kit would put an infected computer in a position to leverage several known vulnerabilities, thus allowing other payloads to be delivered and loaded on the affected system. As such, the Zeus Trojan was slipped onto the now-vulnerable computers where it is armed with the newly-modified weaponry to target and steal banking credentials and many other forms of online authentication details from its victims.
During the investigation of the recent Zeus Trojan attack, researchers were able to track down MWI kit's Command and Control servers pointing to a German IP address. Findings on the server uncovered several MWI-based campaigns, which all utilized different stages of infections and payloads apart from the original Zeus Trojan. Among the targeted IP addresses, 49% of them were found to be machines from Israel.
Check Point researchers claimed, "there are many reasons campaigns can end up with a lopsided geographical distribution of infection victims; that, alone, does not necessarily imply a 'targeted campaign' scenario." While this scenario may be plausible, it was neither the full story nor the exact case of this recent 'Zeus' attack. The full breakdown in percentages of country IP addresses used in the recent campaign can be clearly seen in the graphic below showing Israel as the dominating target.
Zeus Trojan attack IP address locations pie chart - source: Check Point
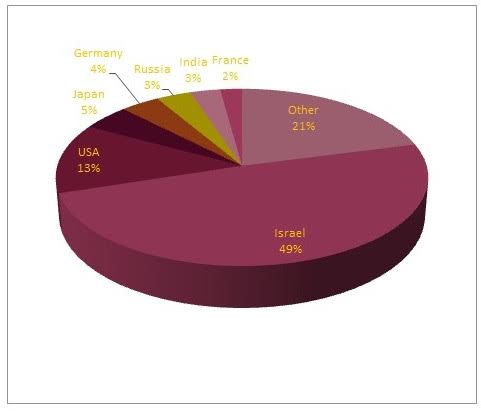
Further analysis of the targeted Israeli IP addresses reveals over 200 PCs in 15 different Israeli locations were targeted, which belong to government agencies, security firms, research agencies, and hospitals in the region. From the IP geo-location and agency attacked data, we can conclude that the attack using an updated variation of Zeus was no accident, and the attackers were looking for specific information during their campaign.