Updated NotCompatible Trojan Ushers in High-Level Sophistication to Turn Android Devices into Relentless Botnets
 Mobile devices are everyone now days and just about everyone who is of proper age has some type of cell phone or mobile device that they access the internet. In the full scope of massive growing popularity of smartphones, hackers are exploiting as many mobile apps as they can.
Mobile devices are everyone now days and just about everyone who is of proper age has some type of cell phone or mobile device that they access the internet. In the full scope of massive growing popularity of smartphones, hackers are exploiting as many mobile apps as they can.
The sophistication of mobile malware has reached a panicle as the NotCompatible Trojan, an Android Botnet, is updated for a third time to now compromise Android devices so that they become virtual zombies under the control of a command and control server.
Botnets have long been known as a massive group of compromised computers, usually desktop machines or servers. Due to the popularity of mobile devices, hackers who exploit such malware have taken their operations mobile mainly to attack devices running the Android operating system. Among the mobile malware threats there is a Trojan called NotCompatible, which has peer-to-peer communication, encryption, and server architecture built-in. This all makes NotCompatible efficient in its ability to recruit Android devices for carrying out malicious actions over the internet. From computer security expert research performed by the firm Lookout, it is evident that NotCompatible is now the most complex and sophisticated Android botnet discovered.
NotCompatible, the NotCompatible.C Trojan, has been monitored since 2012, when at that time it was only used as a proxy on infected Android devices to launch spam campaigns. The latest variant of NotCompatible now employs a two-tiered server architecture. It now connects to a gateway command and control server with a load balancing approach where infected devices from different IP address locations are examined and filtered. In a nutshell, the new NotCompatible Trojan will allow only authenticated clients to connect, making it difficult to detect its actions and give the malware unfettered access to its gateway server. The chart below gives a quick glance at how NotCompatible exactly works.
NotCompatible.C Operation chart – source: Lookout
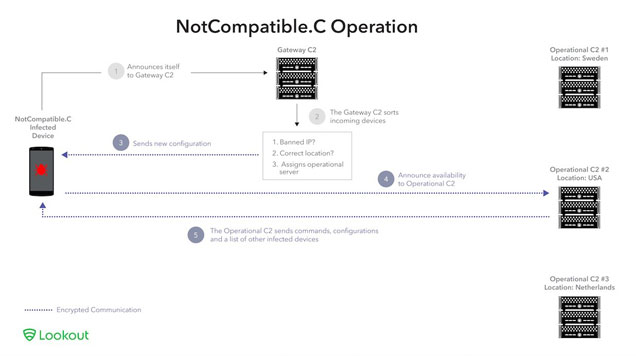
The data transmitted by NotCompatible can be shared with other infected devices, creating a redundancy that makes it nearly impossible to interrupt its efforts of attacking other systems. Just think, this type of malicious activity is waged on other systems all from the launching pad of a mobile device running Android OS.
So far, NotCompaitble servers have reached many countries, including the US, UK, Netherlands, Poland and Sweden. Other analysis of NotCompatible pinpoints its availability being exploited by hackers where the Trojan is up for rent to carry out specific malicious activities. These actions conclude that the hackers behind updating NotCompatible are at a comfort level of dishing out their botnet-creating Trojan to others, which could later be used to attack higher level entities, such as corporate environments across the globe.