SUCEFUL
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 14,588 |
| Threat Level: | 90 % (High) |
| Infected Computers: | 105,065 |
| First Seen: | September 15, 2015 |
| Last Seen: | November 8, 2025 |
| OS(es) Affected: | Windows |
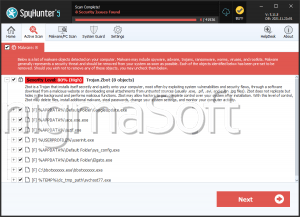
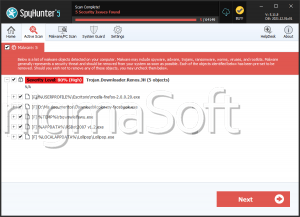
SUCEFUL is a threat that is designed to target Automatic Teller Machines (ATMs) from different vendors to take money from their clients. SUCEFUL may be used to hold and retain cards, disable any alarms on the ATM and read debit and credit card track data. This has made SUCEFUL an alarming new player in the threat world, allowing third parties to collect large amounts of money directly from computer users, as well as having the ability to cause numerous problems.
Table of Contents
The Harmful Actions of SUCEFUL and Other ATM Threats
Since 2013, PC security researchers have been aware of threats that may be used to trick ATMs into dispensing money to unauthorized users. However, PC security researchers have reported the appearance of SUCEFUL, a new threat that is specifically designed to target card holders by attacking them through the affected ATM. SUCEFUL, or Backdoor.ATM.Suceful seems to have been created on August 25 of 2015. SUCEFUL was first uploaded from Russia and is currently going through its development phase.
SUCEFUL can target ATMs from different vendors by targeting the XFS Manager, a platform used by multiple ATMs. The XFS Manager is designed to be independent of any vendor and run anywhere. Unfortunately, this means that threats like SUCEFUL that are designed specifically to target that platform will then be capable of attacking ATMs from multiple vendors. SUCEFUL, in particular, is targeted for Diebold and NCR ATMs.
What can SUCEFUL Do?
PC security analysts have analyzed SUCEFUL and have found that SUCEFUL has the potential to carry out numerous threatening operations on infected ATMs. The following are some of the abilities of SUCEFUL that are currently suspected:
- On NCR or Diebold ATMs, SUCEFUL can read all credit card and debit card track data, meaning that SUCEFUL can collect credit card numbers and carry out various operations.
- SUCEFUL can read data from credit and debit card chips.
- SUCEFUL can disable ATM sensors that may be designed to detect similar threats as well as any kind of possible alarm.
- PC security researchers have noted that SUCEFUL can be controlled using the ATM PIN pad, allowing third parties to retrieve data or send instructions to their threat.
- One of the most alarming aspects of SUCEFUL is that SUCEFUL is capable of holding the victim's card or ejecting it on demand. Third parties may use SUCEFUL to make the affected ATM retain the victim's credit card. When the victim leaves the ATM to ask for help retrieving their card, the attackers can eject and get the card from the affected ATM.
Have SUCEFUL Attacks Been Observed?
SUCEFUL attacks have not been observed in the wild. PC security researchers, therefore, have no evidence on how SUCEFUL is installed on affected ATMs or in what ways this threat is delivered. If SUCEFUL is delivered using methods similar to other ATM threat infections (such as Ploutus and PadPin), then the con artists have to gain access to the targeted ATM. To install the threat, the targeted ATM needs to be opened from the top and then a USB or CD-ROM can be used to transfer the threat infection. In many cases, employees with access to ATMs are bribed to perform these kinds of operations for the people responsible for these kinds of threats. If your card is stuck in an ATM, PC security researchers strongly advise against walking away. Keep your bank's number handy (a number should also be present in most cases in the vicinity of the ATM) so you can look for help without having to leave the ATM and your credit or debit card unguarded.
SpyHunter Detects & Remove SUCEFUL
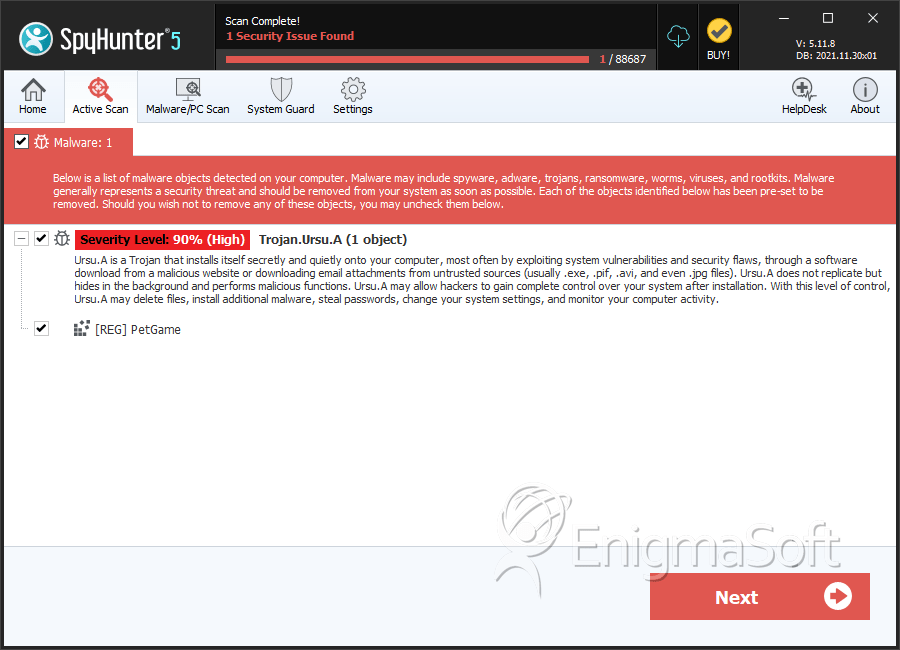
Registry Details
Analysis Report
General information
| Family Name: | Trojan.Ursu.A |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
05028cb6c42afa3c0f88162fa4ed96cd
SHA1:
f89be7fece20f436fd5552e904f971b0bcde99e3
SHA256:
4505DFE008D464402C753E1C1FCF1E4EB5D1B486E52BF67FFBE525148383E6E2
File Size:
740.86 KB, 740864 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have exports table
- File doesn't have security information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Company Name |
|
| File Description |
|
| File Version |
|
| Internal Name |
|
| Legal Copyright |
|
| Original Filename |
|
| Product Name |
|
| Product Version |
|
File Traits
- .NET
- x86
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\users\user\appdata\local\temp\ixp000.tmp\rmm41wz.exe | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\ixp000.tmp\rmm41wz.exe | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\ixp000.tmp\sgt41kb.exe | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\ixp000.tmp\sgt41kb.exe | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\ixp000.tmp\tmp4351$.tmp | Generic Write,Read Attributes,Delete |
| c:\users\user\appdata\local\temp\ixp001.tmp\noi55bm.exe | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\ixp001.tmp\noi55bm.exe | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\ixp001.tmp\seb00mz.exe | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\ixp001.tmp\seb00mz.exe | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\ixp001.tmp\tmp4351$.tmp | Generic Write,Read Attributes,Delete |
Show More
| c:\users\user\appdata\local\temp\ixp002.tmp\kyo67cp.exe | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\ixp002.tmp\kyo67cp.exe | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\ixp002.tmp\mti66.exe | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\ixp002.tmp\mti66.exe | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\ixp002.tmp\tmp4351$.tmp | Generic Write,Read Attributes,Delete |
Registry Modifications
Registry Modifications
This section lists registry keys and values that were created, modified and/or deleted by samples in this family. Windows Registry activity can provide valuable insight into malware functionality. Additionally, malware often creates registry values to allow itself to automatically start and indefinitely persist after an initial infection has compromised the system.| Key::Value | Data | API Name |
|---|---|---|
| HKLM\software\wow6432node\microsoft\windows\currentversion\runonce::wextract_cleanup0 | rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\Ygrbwppu\AppData\Local\Temp\IXP000.TMP\" | RegNtPreCreateKey |
| HKLM\software\wow6432node\microsoft\windows\currentversion\runonce::wextract_cleanup1 | rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\Ygrbwppu\AppData\Local\Temp\IXP001.TMP\" | RegNtPreCreateKey |
| HKLM\software\wow6432node\microsoft\windows\currentversion\runonce::wextract_cleanup2 | rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\Ygrbwppu\AppData\Local\Temp\IXP002.TMP\" | RegNtPreCreateKey |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Process Manipulation Evasion |
|
| Process Shell Execute |
|
| User Data Access |
|
| Encryption Used |
|
| Anti Debug |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
C:\Users\Ygrbwppu\AppData\Local\Temp\IXP000.TMP\sgt41Kb.exe
|
C:\Users\Ygrbwppu\AppData\Local\Temp\IXP001.TMP\sEB00mZ.exe
|
C:\Users\Ygrbwppu\AppData\Local\Temp\IXP002.TMP\kYo67Cp.exe
|