Scammers Exploit Boston Marathon Bombings to Spread Malware Attacks
 The unfortunate bombing events that took place during the Boston Marathon are truly a tragedy, which scammers have already exploited to aid creative malware campaigns spreading multiple types of threats.
The unfortunate bombing events that took place during the Boston Marathon are truly a tragedy, which scammers have already exploited to aid creative malware campaigns spreading multiple types of threats.
It is almost expected, as if this world does not have enough cruel people, that hackers and cybercrooks look to popularized tragedies and news events to exploit, so they may have a basis of spreading malware. The latest online scam related to the Boston Marathon bombings is one that is using the disastrous event's subject to populate the headers of one out of every five spam messages.
It didn't take scammers but a few hours after the incident to start exploiting users through aggressive spam campaigns spreading emails with subject lines related to the Boston explosion. Many of the subjects for these outlandish spam messages read 'Aftermath to Explosion at Boston Marathon' and 'Boston Explosion Caught on Video.'
Obviously, with the curiosity of people nowadays and the probability of news spreading within seconds of a tragedy on social networking platforms, computer users are apt to click links without giving it a second thought or thinking of the potential likelihood of such a link being laced with malware. Not to mention, such spam messages related to tragedies like the Boston bombings are prone to appear on Facebook and Twitter. There is nothing stopping hackers from exploiting the same subject matter on the broad social networking stage, in addition to spreading malicious spam messages.
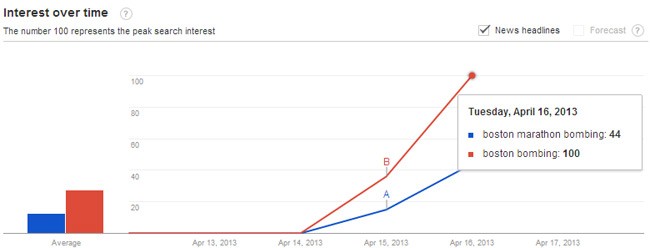
It seems like it was just the other day that hackers were exploiting the news of the Vatican ushering in a new Pope. At the time, there were a number of malware attacks spread through Pope-themed spam messages. Moreover, hackers took it upon themselves to create a fake Pope twitter account to potentially wreak havoc by sharing malicious links. Many times hackers will also lace search engine results with malicious sites related to such a popular event. The image in Figure 1 below shows how the search traffic for the Boston Marathon bombings has spiked in recent days, giving hackers an abundance of people searching the Internet for any trace of new news or media surrounding these tragic events.
Figure 1. - Google Trends for Boston Marathon bombing keywords steadily rising
Below is a list of top related 'Boston Marathon Bombing' terms and spam subjects that you may want to be wary of when performing searches on the Internet or opening emails due to hackers lacing them with malware.
- 2 Explosions at Boston Marathon
- Boston Explosion Caught on Video
- BREAKING - Boston Marathon Explosion
- Aftermath to explosion at Boston Marathon
- Explosions at Boston Marathon
- Explosion at Boston Marathon
- Explosions at the Boston Marathon
- Explosion at the Boston Marathon
- Video of Explosion at the Boston Marathon 2013
The The malware has been identified as
One of the main spam campaigns spreading 'Boston Marathon Explosion' emails comes with a password stealer called Trojan.GenericKDZ.14575, identified by Bitdefender. This particular Trojan is a component of the RedKit browser exploit pack, the same threat used in an attack against users to a hacked NBC website back in February of this year.
There have been reports from researchers uncovering many of these spam messages related to the Boston bombings as having links that install other forms of malware coming out of the woodwork. Some of this malware has been identified as similar Trojans, Packed.Generic.402 and Tepfer-Q, known for loading the following files:
\drivers\npf.sys \Packet.dll \wpcap.dll - boston.avi_______.exe
Another emerging threat, also exploiting the Boston Marathon bombings, is a malicious worm identified as WORM_KELIHOS.NB. This particular worm is responsible for hiding directories on removable drives with the command C:\WINDOWS\system32\cmd.exe F/c "start %cd%\game.exe".
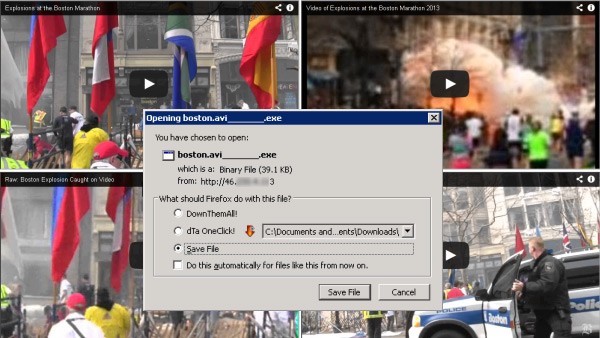
The image in Figure 2 below is an example of a redirected site and file download pop-up from a malicious link in a recent spam message with a Boston Marathon bombing subject line claiming to offer a video of the incidents.
Figure 2 - Malicious website redirect and file download from Boston Marathon Bombing spam message link redirect – source: dataprotectioncenter.com
The Trojan.GenericKDZ.14575 threat is known for pilfering data where it is susceptible to stealing passwords and grabbing users' online account data directly from web browser applications. The underlying theft of data was also found to monitor network traffic, so it can target Bitcoin wallet information, download malware and send out emails at random.
As you may know, when a hacker is armed with the proper personal data or online account login information, one could easily succumb to identity theft or out-right theft of money from an online banking account. The possibilities are virtually endless when such a threat is initiated. Just think, the whole data theft process rooting from the Trojan.GenericKDZ.14575 infection propagates from a Boston Marathon bombing-related email message.
Let this be a clear warning for us all to use extreme caution when opening or loading email messages related to popular news stories or tragedies. Even though we are all anxious to stay abreast of the latest news happenings and updates on the Boston Marathon bombings, we must also restrain from commencing our very own tragedy in the form of a malicious Trojan stealing our personal data.