Mal/Generic-L
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 10,934 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 30,155 |
| First Seen: | October 11, 2011 |
| Last Seen: | February 6, 2026 |
| OS(es) Affected: | Windows |
Mal/Generic-L is a generic name for a backdoor Trojan making its way across cyberspace. A Trojan is a malicious program that cybercriminals build to carry out programming script that steals data and opens a port to allow a hacker remote access.
Cybercriminals exploit software or hardware vulnerabilities and rely heavily on human hands to blindly click and download malicious programs. Trojans hide behind decoys, for instance some fake Adobe Flash update, a special codec needed to view a movie or an infectious link crafted in email spam.
Malware attacks are not limited to personal computers, but a jackpot would be planting and growing a virus inside a large company to target or reach a larger audience. Mal/Generic-L was recently spotted in an email spam campaign targeting trusting employees.
Subject: IT Notice
Message body:
Dear all,
Just a quick alert to let everyone know that our company have experienced a new kind of virus to web space and personal computer. found that the computer system information leaked, such as in other server information is moving, a few files deleted. Expert written virus removal tools to help us fully remove this virus, Please download and install the patch, obtain virus definitions, and run the removal tool. Download the tool from: [LINK]. Please Back Up Your System Databases, If any questions, please do not hesistate to contact IT department.
Because the email appeared to be personalized, in other words it was sent from an internal email account (most likely spoofed), and the link reflected the company's own URL. Many employees may have been fooled into clicking and downloading the virus that was hidden behind the fake link. Victims who clicked it where redirected to a third-party website housing Mal/Generic-L and co-conspirator Troj/Inject-QL, another virus and malicious program, so they could download the 'fix', which of course was the actual infection.
A few telltale signs of a poisonous email, IM message or alert that leads to the download of an infection are:
- Poorly written content or text, i.e. poor grammar, spelling or sentence construction.
- Emails, IM chat messages, Facebook posts, etc., requiring you 'click' on some salacious or innocent- looking link. Before you click, verify the source and, if necessary, enter the official URL in the browser yourself and visit the official website to see if the alert, notice or invite is true.
- A URL in the body of a web page doesn't match the URL in the browser. For instance, if you somehow are presented a fake Youtube or Facebook page and are wondering if it is real, go to the official website and see if the same alert or message is rendered.
All malware carries a single or multiple payloads. At a minimum, Mal/Generic-L in Mal/Generic-L's role as a backdoor Trojan intends to help give a hacker unbridled access and control of your PC.
Once a hacker has administrative control, he can use the infected system to distribute a DNS attack or launch another mass email spam campaign to garner more victims.
If in a corporate environment, hopefully you already know to 'verify' all emails before opening it, especially those of an IT nature. Cybercrooks study social engineering and figure many PC users assume if the 'trap' message asks to double-check, many will not do it and just assume it legitimate. If somehow you clicked too soon, you need to notify your 'real' IT department immediately, so they can quarantine and eradicate the problem.
If the virus is on your personal computer, you should disconnect your Internet to shutdown any communications with a remote server and a hacker. Aggressive malware loves to hide deep in a system's kernel, BIOS or MBR and may be using rootkit technology to mask its file names. If you are not highly skilled in editing these types of files, you should rely on an expert tool known to contain an anti-rootkit component that can find all traces of Mal/Generic-L and safely remove it.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| Fortinet | W32/Swisyn.ATFV!tr |
| Kaspersky | Trojan.Win32.Swisyn.atfv |
| ClamAV | PUA.Win32.Packer.Anti-4 |
| Avast | Win32:Hupigon-OYJ [Trj] |
| McAfee | Generic PWS.o |
| CAT-QuickHeal | Trojan.Swisyn.atfv |
| Fortinet | W32/Jorik_IRCbot.OGL!tr |
| Ikarus | Trojan.ILCrypt |
| AntiVir | TR/Kazy.81851.2 |
| BitDefender | Gen:Variant.Kazy.81851 |
| Kaspersky | Trojan.Win32.Jorik.IRCbot.ogl |
| McAfee | Artemis!4D70D65D1257 |
| AVG | Downloader.Agent2.BCPH.dropper |
| Fortinet | W32/Dropper.DHV!tr |
| McAfee-GW-Edition | Heuristic.LooksLike.Win32.Suspicious.J |
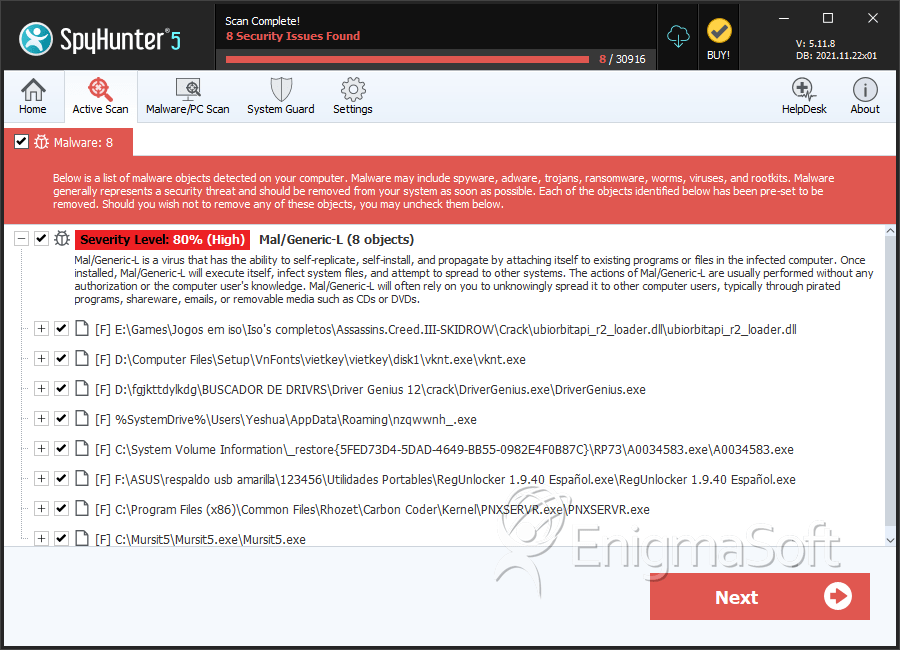
SpyHunter Detects & Remove Mal/Generic-L
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | DriverGenius.exe | ef5eb689e408a53ab97a4501b76b5e29 | 1,148 |
| 2. | ubiorbitapi_r2_loader.dll | 9d24998561a96f192aa2aa6ad5faf3b3 | 675 |
| 3. | vknt.exe | a1b70bd8fca5dc284f9a9506392abd76 | 214 |
| 4. | RegUnlocker 1.9.40 Español.exe | 6d59069e3d9db3160c2340a84dc0d827 | 200 |
| 5. | A0034583.exe | 4f211987b6dfd4c44e91643d5d06f318 | 184 |
| 6. | PNXSERVR.exe | d872e33a600c5e00728144b150420f30 | 79 |
| 7. | Mursit5.exe | f5f342455348718c6dea2467b59d93ef | 74 |
| 8. | huawei_code_tool.exe | 331bc33cbf4b7319129ef05ba684674e | 65 |
| 9. | NWService.exe | 1f840c6150a99ab56c57c0c6b71382f9 | 16 |
| 10. | samurai.exe | 81e041b439aecdf26f83be3342366126 | 8 |
| 11. | IDMan.exe | 2be1530f4dec03c97a8d13973ba96c55 | 6 |
| 12. | syservn.exe | de2751d96e26d71aad537f3cb9d00b3d | 6 |
| 13. | GD1.exe | 8335c71038ebb2da089b290b6b6ae8af | 4 |
| 14. | VKSaver3_install.exe | 234b362941a066f7073565788715eac4 | 3 |
| 15. | divx.exe | 2a69fe9e77d709ba6099f7bce31184b9 | 3 |
| 16. | svcs.exe | c975428b066403ecb1117cab087572e4 | 2 |
| 17. | igfxpers.exe | d60dab4986bd5bfa8f6e54056f77b3ab | 2 |
| 18. | naxhohva.exe | 0c5f9fe1f274c1d0b006e3a837f98c37 | 2 |
| 19. | Norton Partition Magic Updater.exe.Startup | 7d0457cde0f4b7cfc4c1ddc1222d607f | 2 |
| 20. | regsvc32.exe | 7ece718e9f1be3690caf43afa4460f67 | 2 |
| 21. | Loveless.sys | 8ead0964fcc1e389e51c8916f16c0d30 | 2 |
| 22. | TCCheckAgent.exe | 32903035d6c8bae1652391ece6263faa | 2 |
| 23. | notepad.exe | 651f9104a72bd90fa4b37676c4e0240c | 2 |
| 24. | system32csrss.exe | 04d2193061866196c73f0d86c477ec4a | 2 |
| 25. | 4ff904a6aa59d723.sys | 5029b6eb7370f97393b314b543934f4e | 2 |
| 26. | 5A9D.exe | bfaba2dc96095127a7ebe1b63e3d823a | 1 |
| 27. | dREbbSq.exe | ca8111eba6055d77a43e744b919a716f | 1 |
| 28. | STK018M.exe | f7a34cc1d27ef7a24a8f8f25e44fbb86 | 1 |
| 29. | ctfmon.exe | 8f1dde163f91588a7ec13f678abdb25c | 1 |