Koler Android Ransomware Self-Replicates via SMS Disguised as a PhotoViewer App
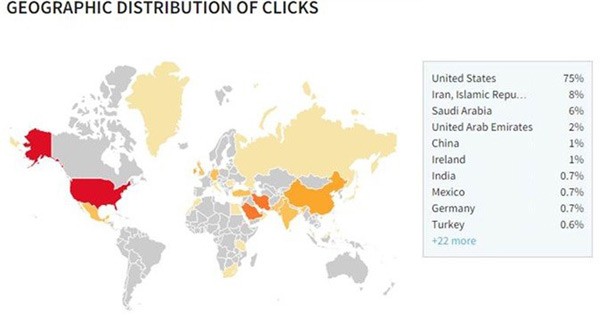
A mobile ransomware with a new self-replicating extortion scheme is threatening the mobile industry. Known as Koler ransomware, the Android ransomware uses a Dropbox-hosted app disguised as a PhotoViewer to target Android users. According to AdaptiveMobile, 75% of Koler victims are US citizens. The SMS distribution mechanism behind Koler ransomware consists of downloading .apk that claims to be just a PhotoViewer and upon installation the ransomware starts working. It sends your IMEI (International Mobile Equipment Identity) number to the criminals, and a Geo-IP operation finds your location. Then, a custom-made law enforcement agency message appears on your screen. The ransomware campaign replicates by sending SMS messages taken from the contact list of the infected device. The Koler ransomware uses the following SMS message to lure mobile users:
'Someone made a profile named -Luca Pelliciari- and he uploaded some of your photos! is that you? http://bit.ly/xxxxxx.'
The bit.ly link lures unsuspecting users to an app claiming to be a PhotoViewer and the app is hosted on the popular Dropbox file sharing service. The bit.ly link downloads IMG_7821.apk (MD5: c7ee04bf3e42640ef6b5015b8af01f4f) and installing leads to getting infected with a variant of the Koler ransomware. Once infected with the Koler ransomware, your screen will be locked and a message pretending to be from your local law enforcement agency will appear. The text goes as follows: 'ATTENTION! Your phone has been blocked up for safety reasons listed below. All the actions performed on this phone are fixed. All your files are encrypted. CONDUCTED AUDIO AND VIDEO'.
Figure 1. Koler Ransomware around the world. Source: AdaptiveMobile
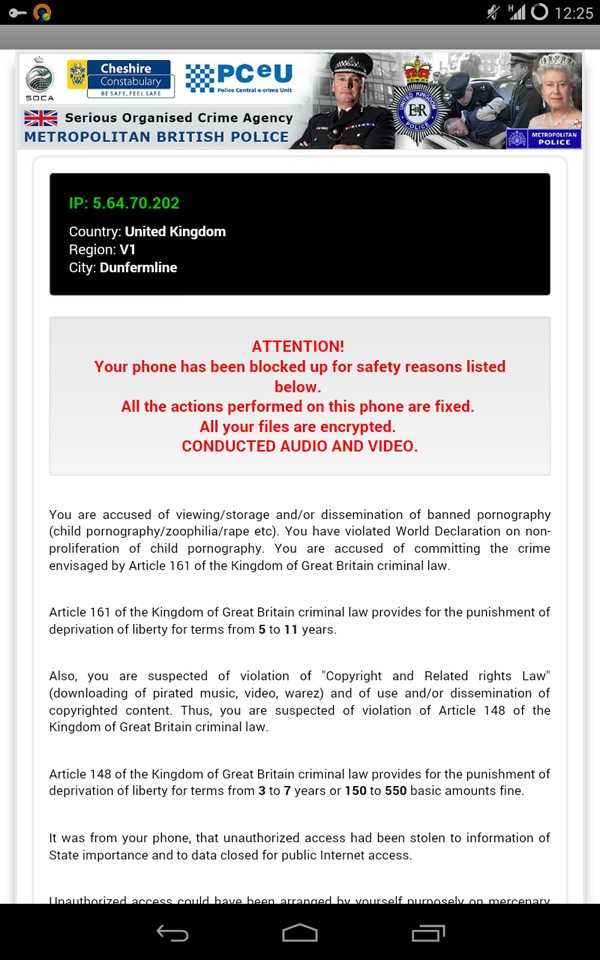
Depending on your location, the message on your screen may differ. Americans will see a message from the FBI Department of Defense, in particular the USA Cyber Crime Center. Users in Great Britain will see a similar message but with imagery depicting Metropolitan Police. Examples of this can be seen in Figure 2 and Figure 3:
Figure 2. Koler ransomware message for United States mobile users. Source: AdaptiveMobile
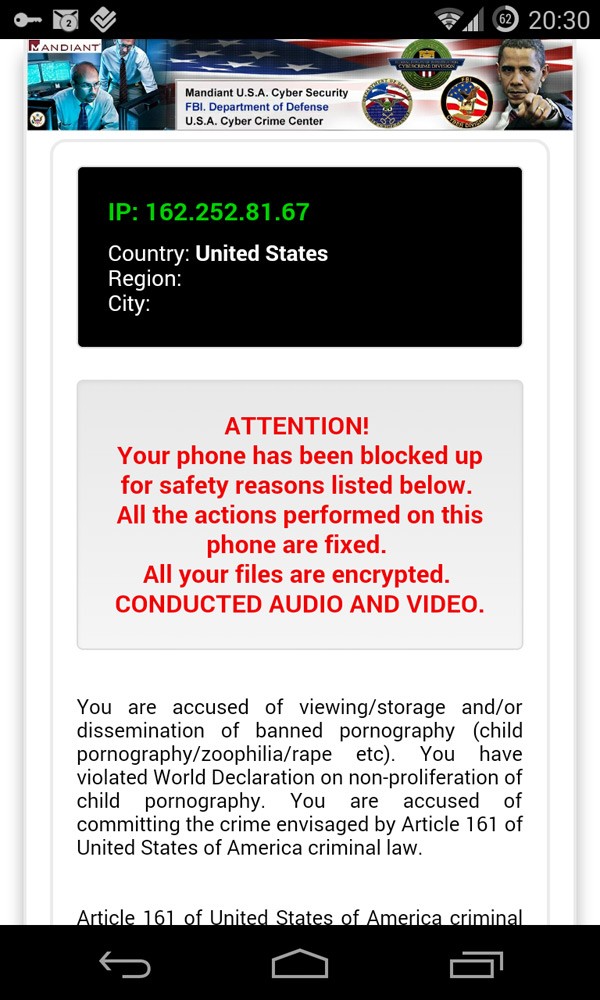
Figure 3. Koler ransomware message for United Kingdom mobile users. Source: AdaptiveMobile
Koler Ransomware Stands Out from Other Mobile Ransomware
Unlike other mobile ransomware, which can spread via SMS by spamming your contacts, the Koler ransomware sends only one SMS, presumably as an attempt to hide any malicious intent or become suspicious. The deployment method consists of three stages:
- The user receives a message from a person within their contacts list, who is already infected. The message suggests that an individual named 'Luca Pellicari' uploaded some of the targeted victim's photos and a link routed through Bitly Link Shortener.
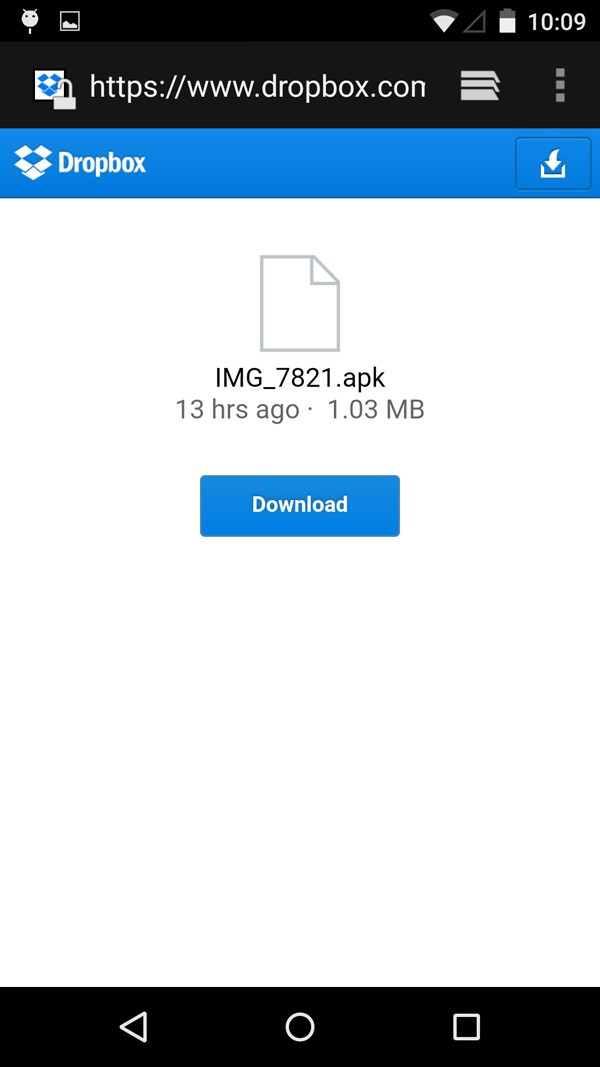
- If the user opens the link, he is directed to a Dropbox page hosting IMG_7821.apk on a Dropbox page show in Figure 4 below.
Figure 4. Koler Ransomware via Dropbox page hosting IMG_7821.apk file. Source: AdaptiveMobile
If the user chooses to install the app, it will appear on his home screen as a PhotoViewer, launching it triggers the Koler infection. The ransomware pretends to take control of your phone and displays a message suited to your location with allegations of viewing and storing child pornography. To unlock the device, the user is forced to pay a certain fee using MoneyPak, Paysafe or Ukash.
- It automatically sends the aforementioned message to all your contacts.
Early in April of this year, the first variant of Koler ransomware resided within various websites with pornographic content and did not use any vulnerabilities to accomplish a stealthy install on an Android device. Instead, it asked for high-level permissions from the smartphone; for example, by displaying a pop-up window with the promise of providing a driver that helps users watch sexy videos. This type of social engineering has paved the way for threats like the Koler ransomware. Koler ransomware has evolved from other well-known mobile ransomware like Selfmite and Samsapo. The Selfmite trojan spreads via SMS. An example of an SMS message distributing Selfmite is 'Dear [NAME], Look the Self-time, http://goo.gl/****** .' The link points to downloading the Self-time.apk. Launching the app causes two events to happen:
- All your contacts receive the same SMS you did;
- The app reroutes you to download mobogenie_122141003.apk. This way the creators get money for this trojan's work.
The Samsapo trojan is much more sinister, because it sends an SMS with text "Это твои фото?" ("Is this your photo?" in Russian) and a link to the poisonous .apk to all of the user's contacts. Once installed on your phone, Samsapo subscribes you to a premium service to trigger its money draining mechanism.
Needless to say, payment of ransom does not guarantee you an unlocked phone, and such practices are not advised because the lack of payment discourages these kinds of attacks. If you install software that's outside Google Play app store, keep in mind that you are entering into dangerous waters. Other app stores still don't maintain the level of commitment to safety as Google. Thus, malware infection is a constant factor with dubious app stores. With the increasing popularity of the Android OS-based devices, there will be more elusive and malicious threats taking advantage of mobile users. How would you react if your Android device is locked and you're being accused of viewing and storing child pornography?