Ai88 Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 28 |
| First Seen: | May 26, 2015 |
| Last Seen: | March 1, 2023 |
| OS(es) Affected: | Windows |
The Ai88 Ransomware is a threat that encrypts victims' files in exchange for ransom. Essentially, the Ai88 Ransomware takes the infected computer hostage, refusing to allow the victim to have access to the encrypted files until a ransom is paid. This ransom is demanded using Bitcoin, an anonymous online currency. Unfortunately, since the Ai88 Ransomware uses an advanced encryption method and the encryption key is not contained in the Ai88 Ransomware files themselves but sent to a third-party, it is almost impossible to regain the encrypted files without paying the Ai88 Ransomware's ransom. Because of this, malware researchers strongly advise computer users to keep a backup of all important files on the cloud or an external device. This can allow computer users affected by the Ai88 Ransomware to restore their files from a backup rather than paying the Ai88 Ransomware's ransom and allowing the persons responsible for this attack to continue abusing computer users.
Table of Contents
How the Ai88 Ransomware and Similar Threats may Attack a Computer
Most ransomware infections like the Ai88 Ransomware are distributed using threat delivery methods that have been around for a very long time. Common Ai88 Ransomware distribution methods include corrupted spam email attachments, social engineering attacks using social media or phishing emails, and attack Websites associated with redirect scripts and exploit kits. In some cases, the Ai88 Ransomware will be disguised as a legitimate program, often distributed through shady Websites and peer-to-peer file sharing networks. A typical example of this is the presence of fake video codecs and Adobe Flash updates distributed using these types of shady methods.
Which Systems are Prone to an Ai88 Ransomware Attack
The Ai88 Ransomware will attack most versions of Windows, both newer versions like Windows 8.1 and some of the oldest still used nowadays such as Windows XP and previous Windows versions. Once the Ai88 Ransomware carries out its attack, computer users are left with no choice but to pay the Ai88 Ransomware ransom to regain access to the encryption key needed to decrypt the affected files.
There have been a marked rise in encryption threat attacks in recent years, most probably matching the increased online presence of inexperienced computer users, which may become prey to threat developers due to a lack of security protections and appropriate precautions. The Ai88 Ransomware targets file extensions associated with productivity programs, online games and media files, all of which are highly likely that computer users will want to recover. The Ai88 Ransomware has features that will delete Shadow Volume copies of infected files, stopping a recovery method that had proven effective against previous versions of these types of tactics.
Protecting Your Files from Hoaxes Like the Ai88 Ransomware
Since it is nearly impossible to recover files encrypted using the Ai88 Ransomware, prevention is the best way computer users can ensure that they do not become victims of these attacks. This means that, first of all, the computer user's files should be backed up. If a computer user has files that would require paying the Ai88 Ransomware's hefty ransom if they were compromised, then it is well worth the investment (often free) in a reliable backup solution for these types of essential files. Once files have been properly backed up, PC security researchers strongly urge computer users to install a reliable, fully updated security application. Apart from anti-malware software, anti-spam filters and firewalls are also important measures computer users can take to protect themselves from the Ai88 Ransomware, particularly in a business environment, where an Ai88 Ransomware attack can be extremely costly and risky to an entire business.
Cultivating proper online behavior is also an enormous part of staying safe online. Computer users should be educated never to open unknown file attachments or click on unknown links. Staying away from high-risk Websites (such as file sharing networks and pornographic Web pages) should also be a priority.
SpyHunter Detects & Remove Ai88 Ransomware
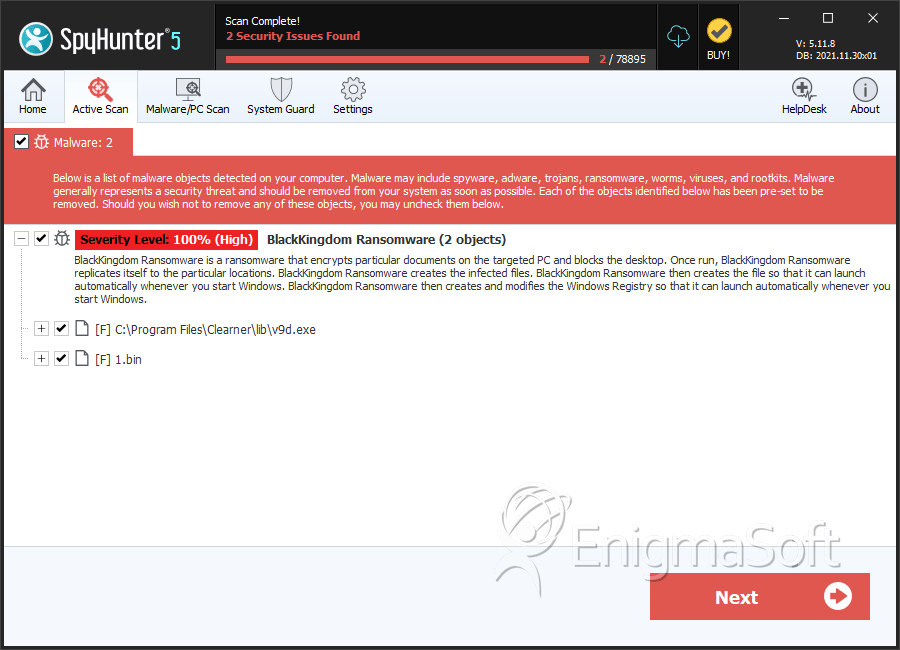
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | v9d.exe | d3206ba6fd5d27f66d45abe1e9a088d3 | 19 |
| 2. | 1.bin | 78177c46ae7665b94de672fcf0a26d8e | 3 |
