Adware Spyware Be Gone
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 19,593 |
| Threat Level: | 20 % (Normal) |
| Infected Computers: | 21 |
| First Seen: | July 24, 2009 |
| Last Seen: | August 12, 2025 |
| OS(es) Affected: | Windows |
This is a fake spyware removal application aimed at tricking the user into purchacing its payed version by repeatedly generating false system security alerts. The program is usually downloaded onto the victim machine by a trojan.
Table of Contents
SpyHunter Detects & Remove Adware Spyware Be Gone
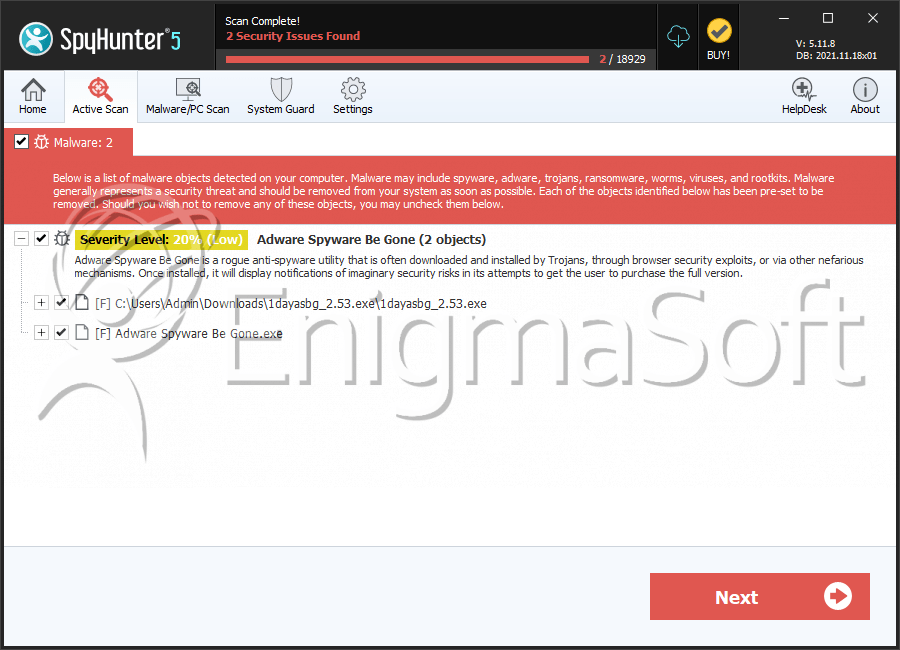
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 1dayasbg_2.53.exe | a12e7302c2bed136fde31f78103ea37e | 6 |
| 2. | Adware Spyware Be Gone.exe | dd85b3b1578ba02f6056eb48453e1105 | 0 |
Analysis Report
General information
| Family Name: | Adware Spyware Be Gone |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
42a7a0bdbe9d20a3a0b0af433b28e632
SHA1:
0ffe20be261128cdd21b1fb87cf120cab839f96c
SHA256:
8260EDFE98F7C8B5B32F5F5E72EF99C4B8858E687E1F32529A7FDEE09522B129
File Size:
2.55 MB, 2552292 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
Show More
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Comments | Created with Setup Factory 6.0 |
| File Description | Setup Application |
| File Version | 6.0.1.4 |
| Internal Name | suf60_setup |
| Legal Copyright | Setup Engine Copyright © 2001 - 2004 Indigo Rose Corporation |
| Legal Trademarks | Setup Factory is a trademark of Indigo Rose Corporation. |
| Original Filename | setup.exe |
| Product Name | Setup Factory 6.0 Runtime |
| Product Version | 6.0.1.4 |
File Traits
- .adata
- .aspack
- ASPack v2.12
- HighEntropy
- packed
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 102 |
|---|---|
| Potentially Malicious Blocks: | 0 |
| Whitelisted Blocks: | 94 |
| Unknown Blocks: | 8 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\users\user\appdata\local\temp\irimg1.bmp | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\irimg2.bmp | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\irimg3.bmp | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\irsetup.dat | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\irsetup.exe | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\irsetup.ini | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\suf6lng.9 | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\windows\spyware begone setup log.txt | Generic Read,Write Data,Write Attributes,Write extended,Append data |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Anti Debug |
|
| User Data Access |
|
| Process Manipulation Evasion |
|
| Process Shell Execute |
|
| Other Suspicious |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
C:\Users\Pqppyfjw\AppData\Local\Temp\irsetup.exe
|