停止Djvu勒索软件
STOP勒索软件家族(也称为STOP Djvu Ransomware家族)是一种威胁很大的恶意软件。尽管STOP Djvu的某些影响文件类型和加密文件扩展名的方法有所不同,但它们只是具有共同特征并起源于STOP勒索软件的多种威胁之一。
最初的STOP Ransomware早在2018年2月就被安全研究人员发现。但是,从那时起,它就得到了发展,其克隆和分支产品家族也不断增加。分发STOP勒索软件的主要方法是使用损坏的附件发送垃圾邮件活动。
STOP Djvu勒索软件的执行方式与同类其他勒索软件威胁类似,对用户可能在其系统中使用的关键文件进行加密和阻止访问。可以对个人文件,图片,文档等进行加密,并且基本上禁止计算机上的所有用户使用。 STOP Djvu勒索软件最初于2018年12月被发现,这似乎是一个非常成功的在线感染活动。研究人员并未意识到勒索软件的传播方式,但后来的受害者报告说,他们在下载密钥源或破解程序后发现了感染。一旦发生渗透,STOP Djvu勒索软件会更改Windows设置,并在文件中附加一系列名称,例如.djvu,.djvus,.djvuu,.uudjvu,.udjvu或.djvuq,以及最近的.promorad和.promock扩展名。较新的版本还没有解密器,但是较旧的版本可以使用STOPDecrypter解密。建议用户无论如何避免支付任何赎金。
用于阻止访问文件的方法使用RSA加密算法。尽管对于没有经验的用户来说,解密文件似乎很困难,但是绝对不需要付出任何努力来支付威胁背后的人员。在这种情况下通常会提供虚假承诺,因此用户付款后很快就会发现它们被忽略了。
STOP Djvu勒索软件的攻击于2018年末首次报道。STOPDjvu的主要分发方法仍然是垃圾邮件,并且针对勒索软件核心的调整相对较小。垃圾邮件中使用的大多数伪造的,受感染的附件都是启用宏的办公文档或伪造的PDF文件,它们在受害者不知情的情况下运行勒索软件。 STOP Djvu的行为也没有太大变化-勒索软件仍会删除所有Shadow Volume快照以摆脱备份,然后开始加密受害者的文件。
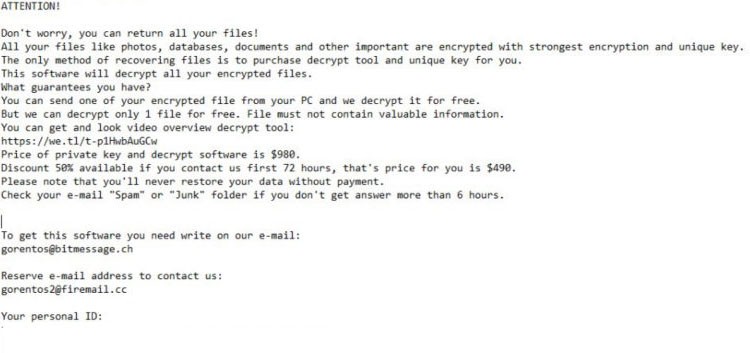
赎金记录有一些细微变化,该记录另存为" _openme.txt"到受害者的桌面。赎金说明的文本可以在这里找到:
'[赎金开始]
————————加密您的所有文件————————
不用担心,您可以返回所有文件!
您所有的文件文档,照片,数据库和其他重要文件均使用最强的加密和唯一密钥进行加密。
恢复文件的唯一方法是为您购买解密工具和唯一密钥。
该软件将解密您所有的加密文件。
我们为您提供什么保证?
您可以从PC发送加密文件之一,而我们将免费对其进行解密。
但是我们只能免费解密1个文件. 文件中不得包含有价值的信息
不要尝试使用第三方解密工具,因为它会破坏您的文件。
如果您在72小时内与我们联系,可享受50%的折扣。
——————————————————————————————————
要获得此软件,您需要在我们的电子邮件中写信:
helpshadow@india.com
保留电子邮件地址与我们联系:
helpshadow@firemail.cc
您的个人ID:[字符串]
[赎金结束]'
勒索软件将自身限制为最初以.djvu扩展名重命名加密的文件,这是一个很好的选择,因为.djvu实际上是由AT&T Labs开发的合法文件格式,用于存储扫描的文档,有点类似于Adobe的.pdf。更高版本的勒索软件对加密文件采用了一系列其他扩展名,包括" .chech","。luceq","。kroput1","。charck","。kropun","。luces","。pulsar1","。 ''.uudjvu','。djvur,'。tfude,'。tfudeq'和'.tfudet'。
可以使用安全研究人员Michael Gillespie开发的所谓的" STOPDecrypter"来免费解密STOP Djvu勒索软件的某些菌株,并可以在线免费下载。
目录
停止Djvu勒索软件视频
提示:把你的声音并观察在全屏模式下的视频。

停止Djvu勒索软件 截图
分析报告
一般信息
| Family Name: | STOP/DJVU Ransomware |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
def8a7bfe5fe47d95a95085d8dbc7a53
SHA1:
7182d4b2f55a560d83edf0824e119f71fa8422b6
SHA256:
B83855EA63E7F28396099A5B6E877BE537E78E4A50DF720262461A1D13B02192
文件大小:
6.29 MB, 6292105 bytes
|
|
MD5:
a6b8c0cb178c31dd347554c3e5a0d5f8
SHA1:
91864f269d696ee80869cfeb3c9a204f8031a3bb
SHA256:
4FFB8E9ADF508662B5E51CBEC75B2E07CE1CBBFAAB873F72EDC7BAC385421E2C
文件大小:
3.47 MB, 3471869 bytes
|
|
MD5:
2336c9624d9a44c393d354206226f508
SHA1:
ea7edc388ad62990f52b9ed40df26d20f4e20190
SHA256:
CE48ED04C92143B7E91F9665DD9337B2EE0B9CC1B5AEE534D26C09E084F8ABB0
文件大小:
1.36 MB, 1359918 bytes
|
|
MD5:
42f32aa699bc45a3638ddeb325ebebc1
SHA1:
508cea3ba2bf04cc6851295f92bf0e752071f6b8
SHA256:
16532B38591B713395C288B11610494BCC4C4537BE492D43C54D66FEB7B95FA4
文件大小:
1.33 MB, 1328186 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has exports table
- File has TLS information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
Show More
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| 姓名 | 价值 |
|---|---|
| Comments | This installation was built with Inno Setup. |
| Company Name |
|
| File Description |
|
| File Version |
|
| Internal Name |
|
| Legal Copyright | Copyright © Alexander Roshal 1993-2022 |
| Original Filename |
|
| Product Name |
|
| Product Version |
|
File Traits
- 2+ executable sections
- big overlay
- HighEntropy
- Installer Manifest
- No Version Info
- RAR (In Overlay)
- RARinO
- SusSec
- vb6
- WinRAR SFX
Show More
- WRARSFX
- x86
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\users\user\appdata\local\temp\is-13e8d.tmp\508cea3ba2bf04cc6851295f92bf0e752071f6b8_0001328186.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-88uan.tmp\ea7edc388ad62990f52b9ed40df26d20f4e20190_0001359918.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-pk5hm.tmp\_isetup\_setup64.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\is-shkd6.tmp\_isetup\_setup64.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Other Suspicious |
|
| Anti Debug |
|
| User Data Access |
|
| Process Manipulation Evasion |
|
| Process Shell Execute |
|
| Keyboard Access |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
"C:\Users\Lehsoaco\AppData\Local\Temp\is-88UAN.tmp\ea7edc388ad62990f52b9ed40df26d20f4e20190_0001359918.tmp" /SL5="$5036E,928289,131584,c:\users\user\downloads\ea7edc388ad62990f52b9ed40df26d20f4e20190_0001359918"
|
"C:\Users\Dfhrhqtz\AppData\Local\Temp\is-13E8D.tmp\508cea3ba2bf04cc6851295f92bf0e752071f6b8_0001328186.tmp" /SL5="$802E8,896816,131584,c:\users\user\downloads\508cea3ba2bf04cc6851295f92bf0e752071f6b8_0001328186"
|



