Are You Sure You’re NOT Infected with Malware?
Don’t Fall Victim to Malware or Ransomware Attacks!
Detect and remove malware, viruses, ransomware & other threats for FREE! Get Protected with SpyHunter.
Download SpyHunter (FREE Trial!)*What is Spyware?
Spyware is one of the most common types of malware that plague both computer and mobile users alike. Due to its overwhelming presence, spyware apps are often called “viruses,” but that is not an accurate description. A computer virus is a separate category that seldom has anything in common with spyware.
The problem with defining spyware is that several different malware categories fall under the same spyware umbrella. Technically, spyware is a type of software that is designed to enter the target system in secret behind the victim’s back. The reason it has the word “spy” in its name is that spyware programs are supposed to gather sensitive information on the infected computer, record it, and then share it with associated third parties.
The interesting thing about spyware is that it can be both legal and malicious. There are legal surveillance programs out there that can be used to monitor online activity for cybersecurity purposes. Think about parents monitoring their children when they surf the web. Or about employers monitoring their employees, making sure they do not waste their time on social media when they are supposed to be working.
Malicious spyware obviously refers to cybersecurity threats that are used to spy upon victims stealthily. And although spyware cannot destroy a system immediately, extensive use of spyware often results in data breaches and private data exploitation. Most of the data theft instances that get reported are in one way or the other associated with spyware. What’s more, aside from private data exploitation, when the system is clogged with spyware, it also slows down the network and device performance. Hence, identifying and removing spyware apps is important to maintain a high level of system performance and data security.
What Is the Main Target of Spyware?
Spyware usually targets private information that can be sold on the darknet. For hackers, no information is useless. Potential victims sometimes wrongly assume that they cannot become a data theft target because they do not have any valuable information. But the basic identity data can be used anytime for a variety of cybercrime activities, and thus, any private data can be stolen. The most common types of data are targeted by spyware campaigns are as follow:
Each type of data can be collected for different purposes. Account logins and PIN codes could be used for identity theft and financial cybercrimes. Email addresses can be hoarded for spam campaigns. Browsing history is often used for shady online marketing schemes, and keyboard input, depending on the data stolen, might be used for a variety of malicious activities, ranging from blackmailing to identity theft.
What Are the Types of Spyware?
Since we have already established that several different malware categories may be considered spyware, let us lay down the main types of spyware. Those are:
To find out more about each category, click on the hyperlinks above. It will lead you to a detailed threat description that will tell you how to recognize and protect your system from each of them.
Now system monitoring tools may also manifest in several different ways. If we are talking about desktop spyware, perhaps the most common type of system monitoring tool is a keylogger. However, spyware can attack anyone who uses a computer or a smart device that is connected to the Internet. Thus, mobile device users are not immune to spyware infections either, and the spyware that attacks mobile devices is usually called “stalkerware.”
Stalkerware often slithers into the mobile device disguised as a system update. Therefore, users have to educate themselves about spyware distribution tactics so that they could remain vigilant and avoid potential infections.
The issue here, once again, pertains to the sheer variety of spyware threats. It means that different threats may employ different distribution methods, and it might be challenging both for individual and corporate users to look out for potential infection vectors. For instance, stalkerware may spread around pretending to be a legal software update. Other types of spyware may reach their victims looking like a normal software download, especially if users tend to download software from third-party websites. It is relatively common for spyware to come bundled with freeware.
How to Avoid Spyware?
Since spyware is one of the most prevalent types of malware, it is only natural that millions of people get affected by it every single year. In 2017, more than 900 million people in 20 countries were affected by cybercrime, losing over $170 billion, and spyware took a big piece of that cake. Every single year, tens of thousands of mobile device users get affected by stalkerware, and that is only the reported cases.
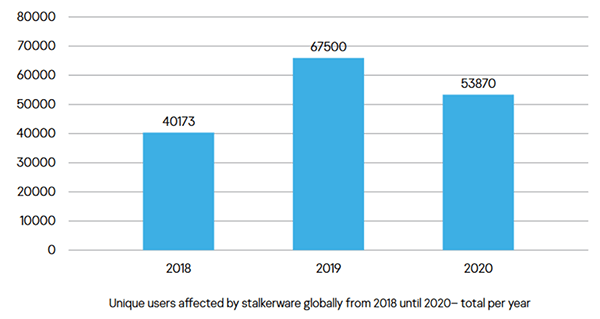
Users affected by stalkerware globally – Source: Kasperskycontenthub
Data thefts result in identity fraud. In the long run, a system overrun with spyware could be one of the causes of a computer crash, and with constant monitoring and exposure to annoying ads, the web browsing experience goes down the drain. This all shows that protection matters even if spyware may not aim at the main system arteries from the very start.
To protect mobile and computer devices, users have to consider employing anti-malware tools. Since spyware may refer to a large number of different infections, a sophisticated security application would make it easier to keep the device and personal data secure.
There are also steps that each user can take to make it harder for spyware to enter their systems. Mobile device users should download apps only from official sources or from trusted publishers. Users should refrain from installing an app they have got from a third-party source. During the app setup, always check permissions. Each app asks for permissions, and users can toggle what data on their device the app can access or not. If the app asks to access a lot of data when it should not, it could be the first red flag that it is a stalkerware application. Finally, mobile device users should avoid clicking on outgoing links in text messages, especially if those texts come from unknown senders.
For desktop users, it is recommended to download and enable a pop-up blocker that will stop annoying pop-ups from interrupting their browsing sessions. Just like with outgoing links in texts for mobile devices, computer users should avoid clicking outgoing links in emails received from unfamiliar parties. Those could be spam email links that promote unreliable software or collect personal data through random surveys. Desktop users should also refrain from visiting unfamiliar websites, especially if they are full of flashy advertisements. Downloading freeware from file-sharing websites may also increase the potential of spyware infection, so users should avoid that, too.
Finally, it is a good idea to check the list of programs that run automatically whenever your OS boots up. There might be spyware apps there, too. And if checking the auto-run list is too challenging, users should always consider employing a security tool for it.
| # | Threat Name |
Severity Level
Severity Level: The determined severity level of an object, represented
numerically, based on our risk modeling process and research, as explained in our
Threat Assessment Criteria.
|
Alias(es) |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|---|
| 1. | MicroBillSys | 60 % (Medium) |
Troj/Banker-EHE Malicious Software Generic Trojan |
13 |
| 2. | Spyware.Look2Me | 60 % (Medium) |
Look2Me Malicious Software Spyware:Win32/Look2Me |
|
| 3. | MediaMotor.Popupwithcast | 60 % (Medium) | ||
| 4. | LightSpy Spyware | |||
| 5. | BadBazaar | |||
| 6. | Spyware.CnsMin | 60 % (Medium) |
PSW.Generic6.AYTG AdWare.CnsMin.I Mal/Generic-A |
|
| 7. | Iopus Email Logger | 60 % (Medium) | 991 | |
| 8. | ISShopBrowser | 20 % (Normal) | ||
| 9. | IMDetect | 60 % (Medium) | 3 | |
| 10. | Dracarys Mobile Malware | |||
| 11. | DivoPlayer | 60 % (Medium) | 4 | |
| 12. | Comscore.C | 100 % (High) | ||
| 13. | SpytechNetVizor | 80 % (High) |
NetVizor application Spyware-Realtime-Spy.dll. Application/Spyagent.A |
|
| 14. | Rogue.AlertSpy | 60 % (Medium) | 2 | |
| 15. | Email-Worm.Zhelatin.agg | 60 % (Medium) |
Troj/BdoorB-Fam Backdoor:Win32/Nuwar.A W32/Nuwar@MM |
|
| 16. | NSPX30 Spyware | |||
| 17. | Worm.Socks.aa | 60 % (Medium) |
WORM_SOCKS.CP Trojan.Drop.Agent.snu W32/Socks.JK!worm |
|
| 18. | Gav.exe | |||
| 19. | Spyware.ReplaceSearch | 60 % (Medium) |
Adware.Searchforit ReplaceSearch SearchForIt |
|
| 20. | RemoteAdmin.GotomyPC.a | 100 % (High) | ||
| 21. | Spyware.SpyMyPC!rem | |||
| 22. | Spyware.Zbot.out | 10 % (Normal) | 6,091 | |
| 23. | Tool.Cain.4_9_14 | 60 % (Medium) |
CainAbel Cain n Abel Malicious Software |
1 |
| 24. | FindFM Toolbar | 60 % (Medium) | 49 | |
| 25. | Dialer.Faretoraci | 60 % (Medium) | 302 | |
| 26. | 4Arcade | 60 % (Medium) | 2 | |
| 27. | MessengerPlus | 60 % (Medium) |
Messenger Plus! MessengerPlus! (threat-l) Application.Messenger.Plus.Q |
906 |
| 28. | SanitarDiska | 60 % (Medium) | ||
| 29. | TorrentSoftware | 60 % (Medium) | 5,357 | |
| 30. | Email-Worm.Zhelatin.vy | 60 % (Medium) |
Backdoor:Win32/Nuwar.A W32/PackTibs.N Email-Worm.Win32.Zhelatin.xv |
3 |
Last updated: 2026-02-07
| Threat Name |
Severity Level
Severity Level: The determined severity level of an object, represented
numerically, based on our risk modeling process and research, as explained in our
Threat Assessment Criteria.
|
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 'There is a problem with this websites security' Fake Message | ||
| 4Arcade | 60 % (Medium) | 2 |
| Accoona | 60 % (Medium) | 1,437 |
| ActionSpy | ||
| AdClicker | 60 % (Medium) | 0 |
| Adware.BHO.BluSwede | 20 % (Normal) | 0 |
| Adware.Insider | 20 % (Normal) | 0 |
| Adware.RelatedLinks | 20 % (Normal) | 1 |
| Android/Spy23C.A | ||
| ANDROIDOS_DROISNAKE.A | ||
| AntiLeech Plugin | 60 % (Medium) | 52 |
| AntiSpyWareSetup.exe | ||
| Application.007_Keylogger | 50 % (Medium) | 2 |
| Application.The_PC_Detective | ||
| Application.Yahoo_Messenger_Spy | ||
| Attor | ||
| Backdoor.Aimbot | 80 % (High) | 1 |
| Backdoor.ForBot.af | 80 % (High) | 1 |
| Backdoor.Servudoor.I | 60 % (Medium) | 11 |
| Backdoor.Win32.Bifrose.bubl | ||
| BadBazaar | ||
| Batavia Spyware | ||
| Belcaro GoldenRetriever | ||
| BitDownload | 60 % (Medium) | 37,193 |
| BondPath |