Are You Sure You’re NOT Infected with Malware?
Don’t Fall Victim to Malware or Ransomware Attacks!
Detect and remove malware, viruses, ransomware & other threats for FREE! Get Protected with SpyHunter.
Download SpyHunter (FREE Trial!)*RAT stands for a remote administration tool. It may also mean remote access tool or remote access trojan, especially in the context of a malware infection. A remote administration tool refers to software that can remotely take full or partial control of a device. In other words, with this software, someone can access your files, camera, turn your computer on and off, and so on.
It is important to note that there could be legitimate RATs, too. For instance, your IT team might use a remote administration tool to fix a problem on your computer at work without the need to come to see you in person. However, since our focus is on malware, we will not discuss different types of legitimate RATs here.
The most common types of malicious RATs are trojans. So, in a sense, it is possible to say that RAT is yet another type of trojan infection. Therefore, just like most of the trojans, a RAT trojan can also be downloaded by accident when users are tricked into thinking that they download a legitimate program (like a game, for example). Once a RAT is installed on a target system, it can perform a variety of actions, depending on what its C2 (command and control center) is telling it to do. Thus, such infection can steal sensitive information, block your keyboard, and even download and install additional malware.
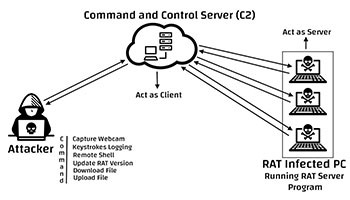
Command & Control Server (C2) RAT action chart – Source: Hackersterminal.com (click for larger image)
Funny enough, RATs first emerged in the 1990s as a way to prank friends between tech-savvy teenagers. They would create early types of remote access tools to slip them into their friends’ computers as a joke. These RATs would open CD-ROM trays, switch mouse button functions, or change desktop colors, making it seem like the machine was possessed. Unfortunately, they were quickly applied in cybercrime activities, too.
According to researcher Veronica Valeros from Czech Technical University in Prague, the number of RAT infections really took off in the 2010s. In the 2000s, there were 70 RAT infections detected worldwide, whereas, in the 2010s, at least 250 different types of RATs were detected. The number might seem small compared to most of the other malware detections, but it is important to emphasize that, unlike ransomware families that come and go, RAT infections tend to last longer. They could be utilized and customized for many years, so there is no need to create multiple RATs when each can be applied several times by different attackers.
The original RATs were intended for machines that run on Windows, but lately, there are RATs out there that also target Mac, Linux, and Android devices. These programs have become essential parts of cybercrime activities, and they are employed by cybercriminals, state-funded hackers (for cyber warfare), and even stalkers.
Probably the most infamous RAT infections of the 2000s are Gh0st and PoisonIvy. Gh0st was developed by the Chinese and first appeared in 2001. However, it gained track a few years later, when it was used to target economic, media, and political organizations in more than 100 countries. Almost anyone could acquire and use Gh0st because it was available for download in public. A little bit of searching could lead one to the RAT’s download page.
The same could be said about PoisonIvy. This RAT first appeared in 2005, and it was available for download free of charge from the very beginning. Thus, potential attackers did not need to create malware on their own. They could just get the infection and then use it for their own purposes. Some of the high-profile infections carried out with PoisonIvy include the RSA SecurID authentication tool breach and the Nitro attacks on chemical companies. Both campaigns happened in 2011. Needless to say, those were not the only instances of PoisonIvy’s application. The RAT is well-known for its use in espionage campaigns against defense contractors, chemical makers, human rights groups, and government agencies.
Like most malware, RAT has trends, too. As mentioned, longevity is the key point of these infections, but the 2010s saw RATs turning into a cyberworld commodity. In other words, potential attackers do not need to develop these programs themselves. One can purchase or even commission a RAT to be built or an existing infection to be modified based on their requests. RAT developers can easily take note of what the customers want and add more functions to their product.
The lines between remote administration tool and remote access trojan get blurred, too. Take Quasar, for instance. This application is promoted as a remote administration tool, but it can be easily used in dangerous cybercrime campaigns. It works on several Windows platforms and, if applied in a certain way, can cause a lot of damage.
The same can be applied to NetWire and WebMonitor, which are RATs that can affect Mac, Linux, and Android devices. As a matter of fact, the number of RATs that target the Android OS is constantly growing.
However, despite the seemingly growing number of new infections, researchers note that they are not too diverse. They are rather standardized, and their behavior often follows the same pattern. Some of the RATs can be customized, however. The developer may add builder, crypter, or plugins to the basic set. A builder can create a new RAT server upon infection. Instead of connecting to a preexisting server through a predetermined port, a RAT with a builder would have an entirely new server to connect to.
Plugins would add new capabilities to a RAT, and a crypter could help the infection avoid detections by an anti-malware solution. This is possible because a crypter encrypts the program’s code and then decrypts it when necessary, thus obfuscating the infection from a security tool that is on the lookout for a malicious code that is not encrypted.
While some of the RATs are available for free, they can also be sold for anything from $20 to $250 apiece. Presumably, additional functions and capabilities result in a higher price. But in general, a RAT will do what its owner tells it to do because it behaves like any other trojan out there.
It is not that hard to avoid RATs, but one has to know what dangers might await behind a stray link or an unfamiliar file. That said, it is necessary to have an active firewall and keep all of your software updated. Updates patch up software vulnerabilities that might be exploited by RATs.
Consequently, all software should be downloaded only from official sources because illegal downloads are not only criminal activity, but they could bring malware with the software you want to have. It would also be a good idea to regularly back up your data to avoid potential damage from ransomware and other trojan infections. With that covered, you should also learn to ignore random pop-ups and links that urge you to click them. The same can be said about attached files that come with spam email or from people you do not know. Trojans and ransomware often travel via spam, so you will do yourself a favor if you ignore such emails.
Also, you should consider scanning your system regularly with a powerful anti-malware tool. If you notice that your internet connection has been rather slow without any apparent reason; if your files get modified or deleted, you notice unfamiliar processes in Task Manager, or you see unknown programs in Control Panel, it is definitely the time to run a full system scan.
| # | Threat Name |
Severity Level
Severity Level: The determined severity level of an object, represented
numerically, based on our risk modeling process and research, as explained in our
Threat Assessment Criteria.
|
Alias(es) |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|---|
| 1. | Elf 1.0 | |||
| 2. | ModeloRAT | |||
| 3. | JelusRAT | |||
| 4. | NodeCordRAT Malware | |||
| 5. | Silver Fox ValleyRAT Malware Campaign | |||
| 6. | 'SIDDHIVINAYAK' Email Scam | |||
| 7. | BIOPASS RAT | |||
| 8. | DLRAT Malware | |||
| 9. | ShellClient Malware | |||
| 10. | TigerRAT | |||
| 11. | SingleCamper RAT | |||
| 12. | SQLRat | |||
| 13. | Cobian RAT | |||
| 14. | LightlessCan Malware | |||
| 15. | CetaRAT | |||
| 16. | ApolloRAT | |||
| 17. | PyVil RAT | |||
| 18. | Winos RAT Malware | |||
| 19. | JhoneRAT | |||
| 20. | KASIKORNBANK Email Scam | |||
| 21. | Atroposia RAT | |||
| 22. | ElectroRAT | |||
| 23. | BankBot RAT | |||
| 24. | 'Stromag' Email Scam | |||
| 25. | RadRAT | |||
| 26. | Spectre RAT | |||
| 27. | L3MON RAT | |||
| 28. | TEARDROP Malware | |||
| 29. | AllaKore RAT | |||
| 30. | EncryptRAT |
Last updated: 2026-02-08
| Threat Name |
Severity Level
Severity Level: The determined severity level of an object, represented
numerically, based on our risk modeling process and research, as explained in our
Threat Assessment Criteria.
|
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 'ICLOUD Outlook Storage' Email Scam | ||
| 'Kuwait Airways' Malicious Emails | ||
| 'SIDDHIVINAYAK' Email Scam | ||
| 'Stromag' Email Scam | ||
| 'We Receive Another Bank Information' Email Scam | ||
| 'WebMail Server Manager' Email Scam | ||
| 'Your E-mail Will Be Closed' Email Scam | ||
| 9002 RAT | ||
| Abaddon RAT | ||
| Agent Tesla | ||
| AhMyth RAT | ||
| AhRat | ||
| AIRAVAT RAT | ||
| AIVARAT Mobile Malware | ||
| Alien Spy | ||
| AllaKore RAT | ||
| AndroRAT | ||
| AntiHacker | 20 % (Normal) | 4,861 |
| ApolloRAT | ||
| ArrowRAT | ||
| AsyncRAT | 80 % (High) | 254 |
| ATMitch | ||
| Atroposia RAT | ||
| Aurora Malware | ||
| Autospy | 80 % (High) | 0 |